Reference
Refer to this page for details about how Cloudflare orchestrates VPN connectivity to your cloud networks.
Cloud on-ramps
AWS
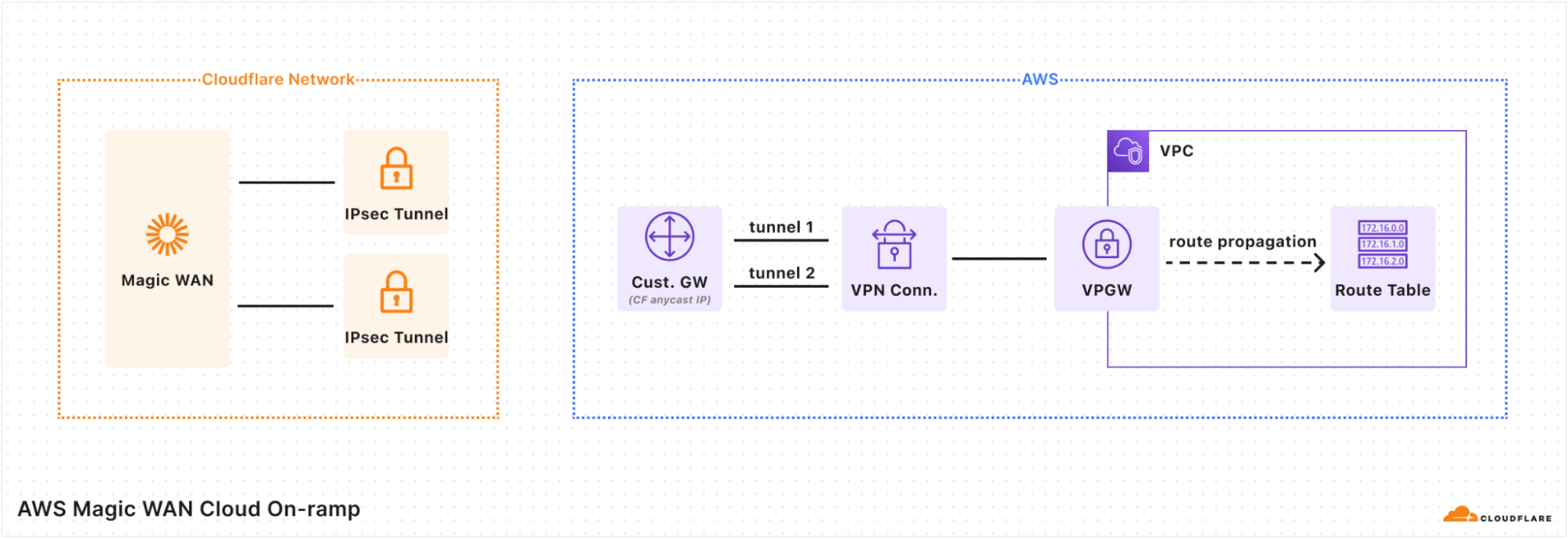
When using Magic Cloud Networking to automatically create on-ramps to your AWS account, you should be aware of the following configuration changes Cloudflare will make on your behalf:
- Cloudflare will create a new Network Security Group (NSG) named Cloudflare Magic WAN with rules allowing outbound/inbound traffic to/from Magic WAN. You must attach this NSG to subnets or virtual machines (VMs) you wish to have connectivity to Magic WAN.
- Cloudflare will create a Virtual Private Gateway and attach it to your Virtual Private Cloud (VPC). If an existing Virtual Private Gateway is already attached to the VPC, on-ramp creation will fail.
- Cloudflare will enable route propagation from the Virtual Private Gateway into all route tables in your VPC. This will result in a route for each prefix in your Magic WAN Address Space targeting the gateway.
- Cloudflare will add a route in Magic WAN for each IPv4 CIDR block in your VPC.
Azure
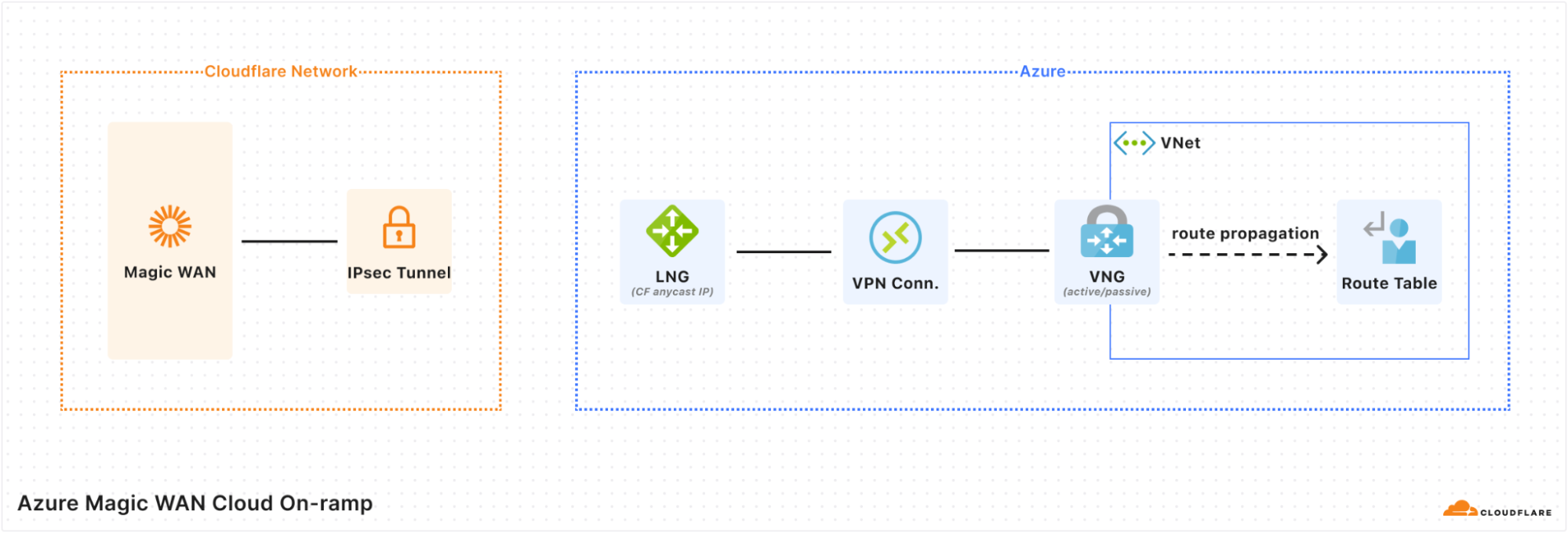
When using Magic Cloud Networking to automatically create on-ramps to your Azure account, you should be aware of the following configuration changes Cloudflare will make on your behalf:
- Cloudflare will create a Virtual Network Gateway in your Virtual Network (VNet). Virtual Network Gateways in Azure require a subnet named
GatewaySubnet. Cloudflare will create aGatewaySubnetif one does not already exist in your VNet. If there is not enough unused address space left in your VNet to create aGatewaySubnet, or if aGatewaySubnetexists but does not have enough address space left for a Virtual Network Gateway, on-ramp creation will fail. - Cloudflare will enable gateway route propagation on all route tables in your VNet. This will result in a route for each prefix in your Magic WAN Address Space pointing to the gateway. If your VNet has other Virtual Network Gateways, their routes will also propagate to your route tables. If you delete the on-ramp, route propagation will not be disabled.
- By default, Network Security Groups in Azure contain Allow rules for outbound/inbound traffic to/from the
VirtualNetworkservice tag, which includes Virtual Network Gateway address space (and therefore your Magic WAN Address Space). If you do not want all resources in your VNet to be accessible from Magic WAN, add the appropriate Deny rules to your Network Security Groups (NSGs). - Cloudflare will add a route in Magic WAN for each IPv4 address range in your VNet.
Supported resources
Magic Cloud Networking discovers the following resource types.
AWS
- AWS Customer Gateway
- AWS Egress Only Internet Gateway
- AWS Internet Gateway
- AWS Route Table
- AWS Subnet
- AWS VPC
- AWS VPC IPv4 CIDR Block Association
- AWS VPN Connection
- AWS VPN Connection Route
- AWS VPN Gateway
Azure
- Azure Virtual Network
- Azure Subnet
- Azure Route Table
- Azure Virtual Network Gateway
- Azure Local Network Gateway
- Azure Public IP
- Azure Virtual Network Gateway Connection
- Azure Route
- Azure Subnet Route Table Association
GCP
- Google Compute Network
- Google Compute Subnetwork
- Google Compute VPN Gateway
- Google Compute VPN Tunnel
- Google Compute Route
- Google Compute Address
- Google Compute Router
- Google Compute Interconnect Attachment
- Google Compute HA VPN Gateway